Memorial Day weekend is here—and for many West Michigan business owners, that means taking a much-needed break. Whether you’re headed to the lake, hosting a backyard barbecue, or simply closing the laptop for a few days, the last thing you want is to be dealing with a tech emergency while you're out.
But before we dive into tech checklists, we want to take a moment to honor the reason for this holiday: to remember and be thankful for the men and women who gave their lives in service to our country. It's because of their sacrifice that we’re able to enjoy the freedom and opportunity we often take for granted—even in something as simple as a long weekend.
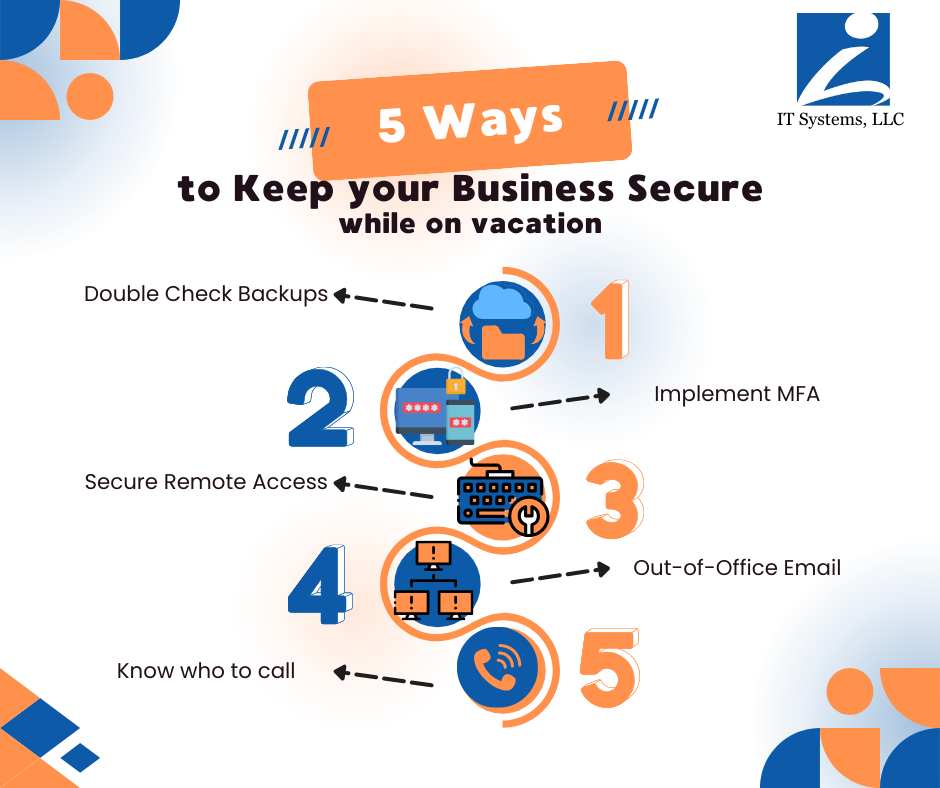
Before you unplug, here are 5 simple things you can do to keep your business secure, connected, and stress-free—even if you’re completely offline.
1. ✅ Double-Check Your Backups
You don’t want to come back on Tuesday to a ransomware attack or lost data from a power outage. Make sure your systems are backed up (ideally off-site or to the cloud), and that those backups are actually working.
🔒 At IT Systems, we help clients across West Michigan set upautomated, encrypted backupswith easy recovery options.
2. 🔐 Enable Multi-Factor Authentication (MFA)
If you're still relying on just a password to protect your business systems—this is your sign to upgrade. MFA adds a second layer of protection by requiring a verification code from your phone or email. That way, even if a password gets leaked, your system is still protected.
🎯 Bonus: Enable MFA for your email, file sharing tools, accounting software, and remote desktop logins.
3. 📡 Secure Remote Access (or Disable It Temporarily)
If your employees are logging in remotely over the holiday weekend, make sure they’re doing it securely. Use a VPN (virtual private network), and avoid letting people log in from public Wi-Fi or unmonitored personal devices.
Not planning on working? Consider disabling remote access for the weekend just to be safe.
👥 If you’re not sure who can access what, we can help you audit your permissions and access controls.
4. 📬 Set an Out-of-Office Email That Doesn’t Invite Hackers
Be cautious about what your auto-reply says. Hackers monitor bounce-backs and out-of-office messages looking for gaps in security. Keep it simple and professional—avoid oversharing dates or travel info.
Good Example:
“Thanks for your message. Our office will be closed for Memorial Day and will respond upon return. If this is urgent, please contact our support team.”
5. 🚨 Know Who to Call If Something Goes Wrong
Make sure you (and your team) know who to reach out to in case something goes sideways while you're away.
Create a quick contact list that includes:
- Your IT provider
- Emergency vendors (ISP, phone systems, power backup)
- A backup contact if you’re unreachable
📞 Our clients have peace of mind knowing we’re just a call or ticket away—even over holiday weekends.
🧠 Final Thought: Tech Shouldn’t Be the Thing That Ruins Your Weekend
Taking time off is important. It helps you recharge, refocus, and come back stronger. And while you’re enjoying the slower pace of the weekend, your systems should be secure, monitored, and working quietly in the background.
More importantly, we hope you take a moment this Memorial Day to reflect on those who made the ultimate sacrifice so that we can live, work, and thrive freely. We’re grateful, and we don’t take that lightly.
If you’re unsure whether your business is protected while you're away, we’re happy to do a quick check-up or walk through a cybersecurity readiness review.
👉 Schedule a free consultation with our team
From our team to yours—wishing you a safe, restful, and meaningful Memorial Day weekend.
—-
IT Systems, LLC
Proudly serving small businesses across Grand Rapids and West Michigan.