Let’s be real...running a business in West Michigan is already enough work without worrying about hackers. But here’s the truth: small businesses are a favorite target for cybercriminals. Why? Because most owners assume “that won’t happen to me” and don’t put strong protections in place.
That’s where a firewall comes in. Think of it like the security guard at the front desk of your office. It decides who can walk in and who gets turned away. Without it, anyone could waltz right in...including people you definitely don’t want near your data.
In this guide, we’ll walk you through why firewalls matter, how to set one up, and how to keep it running smoothly
The Rising Importance of Network Security for Small Businesses
Let’s start with a simple truth: small businesses get hacked all the time. In fact, cybercriminals love targeting smaller companies because they know resources are tighter and IT isn’t always top of the to-do list.
Here’s what that can look like in real life:
- A private school in Grand Rapids has parents’ financial records stored on their system. Without proper network security, that’s easy pickings for a hacker.
- A local dentist’s office in Holland might think their practice is “too small” to matter — but ransomware can shut down their scheduling system and cost thousands in lost appointments.
- A nonprofit in Kalamazoo with donor lists and bank info could lose trust (and funding) overnight if their data is exposed.
And beyond the obvious risks, there are compliance rules like HIPAA for healthcare or FERPA for schools. Failing to meet those can mean fines, lawsuits, and a serious hit to your reputation.
So no, network security isn’t just for the “big guys.” It’s just as important here in West Michigan for businesses with 20 computers as it is for corporations with thousands.
What Exactly Does a Firewall Do?
If the word firewall makes you think of firefighters and hoses, you’re not alone. The name comes from the idea of creating a barrier that keeps fire from spreading — and in the digital world, it works the same way.
A firewall is like the bouncer at the door of your favorite West Michigan brewery. They check IDs, make sure no one sketchy gets inside, and keep the crowd under control. In your business, the firewall checks every bit of traffic trying to come in or go out of your network and decides: Do we let this through or not?
Here’s what that means in practice:
- Blocks unwanted guests: Just like you wouldn’t let strangers into your office without checking who they are, a firewall blocks suspicious visitors from entering your system.
- Stops data from walking out the door: Imagine if someone tried sneaking confidential files out in a backpack. A firewall can catch that and shut it down.
- Protects against common attacks: Malware, phishing attempts, and random “drive-by” hackers scanning the internet for easy targets — a firewall helps keep them out.
Now, here’s where many small business owners get tripped up: the Wi-Fi router that came from your internet provider? It’s like having a screen door on your business instead of a steel lock. Yes, it keeps the bugs out, but anyone determined enough can still push through.
That’s the difference between consumer-grade protection (what most homes have) and business-grade firewalls (what companies like yours need).
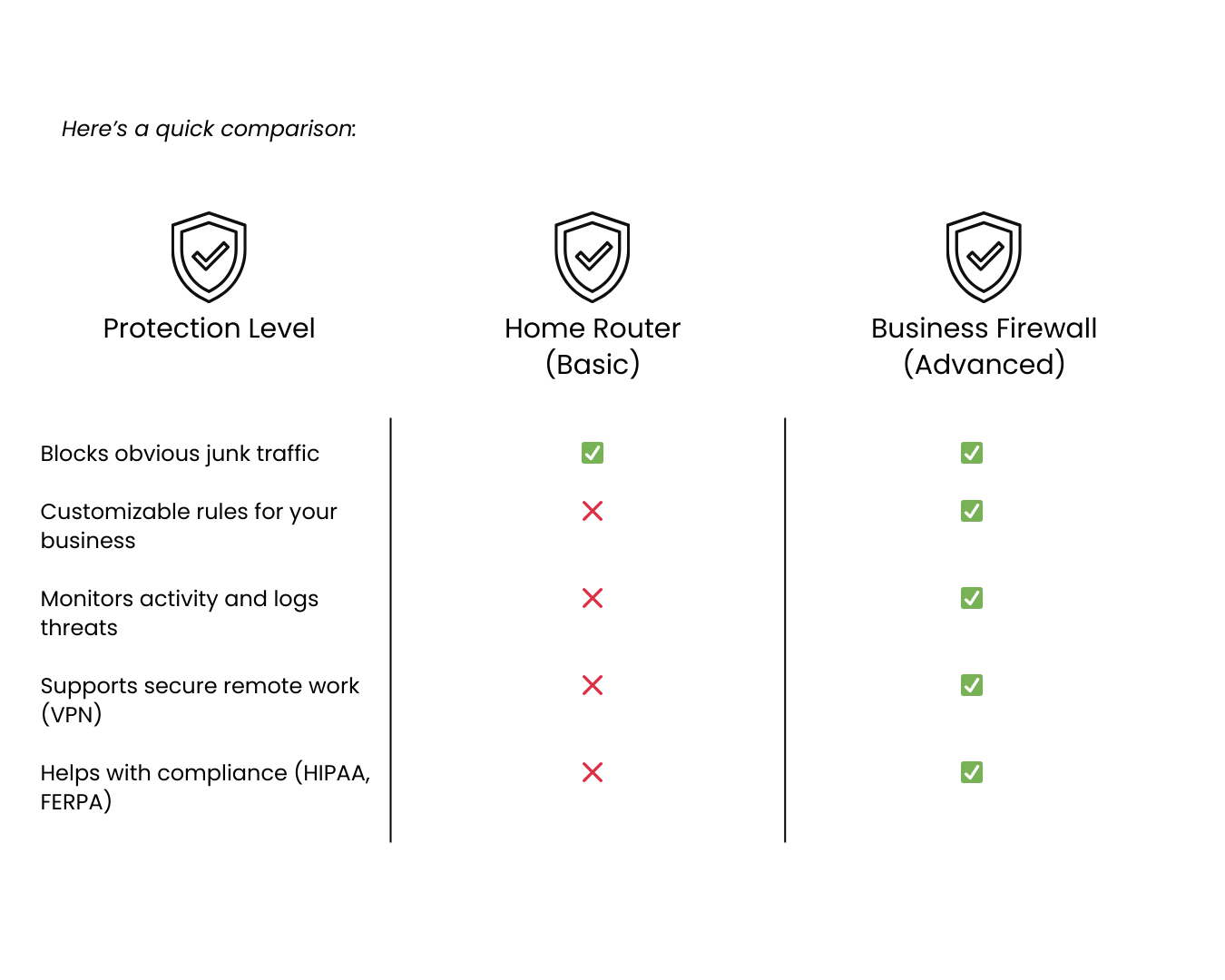
Bottom line: a firewall is the digital lock, bouncer, and security guard all rolled into one. Without it, your network is wide open to whoever decides to jiggle the handle.
Types of Firewalls and Which One Fits Your Business
Here’s the part where things can get confusing, because there’s more than one type of firewall. But don’t worry...I’m going to break this down without the tech jargon.
Think of firewalls like locks: you wouldn’t use the exact same lock for your front door, your car, and your gym locker. Same idea here. Different businesses need different types of firewalls depending on size, budget, and how you work.
Hardware Firewalls
This is a physical device that sits between your network and the internet. Picture it like a security gate outside your office building. Everyone, from employees, to clients, even delivery drivers, has to pass through before reaching your front door.
Best for:
- Offices with multiple computers connected to one network
- Businesses that want one strong line of defense for the whole building
Software Firewalls
Instead of one big gate, this is more like having locks on every single office door. A software firewall is installed directly on each computer or server.
Best for:
- Solopreneurs or micro-businesses (think: one to three people with laptops)
- Extra protection for individual devices, especially if employees take them home
Cloud-Based Firewalls
Here’s where things get modern. A cloud firewall is managed online instead of sitting in your office. It’s like having a security team watching over your business 24/7 from a command center, no matter where your employees are logging in from.
Best for:
- Businesses with remote or hybrid teams
- Private schools or nonprofits where staff work from different campuses or homes
- Companies that don’t want the hassle of managing physical hardware
So Which Firewall Is Right for You?
Here’s a simple way to decide:
- If you’re a two-person landscaping company running QuickBooks and email, software firewalls on each laptop may be enough.
- If you’re a 15-person dental practice in Grand Rapids, you probably need a UTM firewall to keep patient data safe and your team HIPAA-compliant.
- If you’re a nonprofit with staff working remotely in Holland, Muskegon, and Kalamazoo, a cloud-based firewall may fit better.
Another bottom line: the “best” firewall isn’t about having the fanciest gear. It’s about choosing the one that makes sense for how your business actually works day to day.
How to Set Up a Firewall: Step-by-Step for Small Businesses
Okay, so you’ve decided your business needs more than that screen-door Wi-Fi router. Good call. Now let’s walk through the basics of setting up a firewall. Don’t worry...you don’t need to be an IT pro to follow this, but you do need to understand the steps so you know it’s done right.
Step 1: Assess Your Network
- Start by asking: What am I protecting?
- Do you store patient files?
- Do you have staff logging in from home?
- Do you take credit card payments?
A landscaping company with five laptops has different risks than a healthcare practice with sensitive patient data. Knowing what’s most important helps you set the right level of protection.
Choose the Right Firewall
Use the examples from the last section as your guide. Match the firewall to your business size and daily workflow.
Install the Firewall
Hardware firewall: A device gets hooked up between your internet and your network. Think of it as installing a security gate outside your driveway.
- Software firewall: You download and install it on your computers, like putting locks on each office door.
- Cloud firewall: It’s all handled online, so setup looks more like creating accounts and connecting them to your systems.
For most businesses, this is where calling in the pros (👋 IT Systems, LLC) saves time and headaches.
Define Security Policies
This is where you tell the firewall how strict to be. Example:
- Allow employee laptops to connect to work files but block unknown devices.
- Keep ports closed that your business doesn’t use.
- Filter out “time-wasting” or risky websites if you want.
Think of this step as writing the rulebook for your digital front door.
Enable Logging & Monitoring
Your firewall is constantly checking who’s knocking. Logging keeps a record so you can look back and see if anything unusual happened. Without logs, it’s like having a security camera that isn’t recording.
Test Your Setup
Before you celebrate, test it. Try connecting in ways you don’t want allowed and see if the firewall blocks it. Run a vulnerability scan. This step is like checking that your new locks actually latch before you close up shop for the night.
Quick Setup Checklist
- Know what data you’re protecting
- Pick the firewall that fits your size & industry
- Get it installed (hardware, software, or cloud)
- Set clear rules for traffic in and out
- Turn on logging & monitoring
- Test it before calling it “done”
Keeping Your Firewall Effective (Best Practices + Mistakes)
Here’s the truth: setting up a firewall is only half the job. Think of it like buying a brand-new lock for your office...if you never oil it, never check it, and give spare keys to everyone without keeping track, it’s not going to protect much for long.
To really get your money’s worth, here’s how to keep your firewall doing its job day after day:
Best Practices for Ongoing Protection
- Keep it updated.
Cyber threats change fast. If you don’t install updates, it’s like leaving the front door unlocked because you didn’t bother to change the broken latch. - Review the rules every so often.
Businesses evolve — maybe you added remote workers, new software, or online payments. Firewall settings that worked last year might not fit today. A quick quarterly review keeps everything aligned. - Pay attention to the logs.
Your firewall is quietly writing down every attempt to get in. If you never look at the logs, you’re ignoring the sticky notes your security guard is leaving you about suspicious activity. - Train your team.
A firewall can only do so much if your staff are clicking phishing emails or sharing passwords. Teach them the basics: don’t click strange links, use strong passwords, and ask before connecting outside devices. - Have a backup plan.
Even the best security can’t stop everything. Make sure you’ve got reliable data backups and a plan if something goes wrong.
Common Mistakes Small Businesses Make
- Relying on default settings.
Out-of-the-box settings are a hacker’s best friend. Always customize your firewall to match your business needs. - Overcomplicating things.
Some businesses pile on rules until the firewall is harder to manage than their actual work. Keep it clear and simple. - “Set it and forget it” mindset.
Firewalls aren’t crockpots. You can’t just plug them in, walk away, and hope for the best. They need attention. - Not testing after changes.
Any time you update rules or add devices, test it. It’s like checking the doors and windows before locking up at night.
Second to last bottom line: your firewall isn’t a one-time purchase. It’s an ongoing layer of protection that needs a little care. When maintained properly, it runs quietly in the background so you can focus on your business without losing sleep over cyber threats.
Firewalls as Part of a Bigger Security Plan (Layered Defense + FAQs + Local CTA)
Here’s the deal: a firewall is powerful, but it can’t do everything on its own. Think of your business security like layers of an onion (or layers of winter gear here in West Michigan). The firewall is your heavy coat — it blocks the cold wind. But you still need gloves, boots, and maybe a hat to stay fully protected.
Layered Security in Plain English
A strong firewall should be part of a bigger plan that includes:
- Antivirus software: Think of this as bug spray for your computers. It kills the little pests that sneak past the front door.
- Strong passwords & multi-factor authentication (MFA): Locks on the inside doors. Even if someone breaks in, they can’t just wander around.
- Regular data backups: Your fire extinguisher. If something gets through, you can recover without losing everything.
- VPNs for remote work: A private tunnel for employees logging in from home or the coffee shop, instead of leaving their connection wide open.
When you layer these tools together, you’re much harder to hack and they usually move on to an easier target.
FAQs: Quick Answers for Busy Business Owners
Do I really need a firewall if I already have antivirus?
Yes. Antivirus is like locking your desk drawer, but a firewall locks the entire office. You need both.
How much does a firewall cost?
It depends on your size and needs. For a small business, the investment is often less than the cost of one day of downtime from a cyberattack.
What’s the difference between a firewall and a VPN?
A firewall filters who gets in and out. A VPN creates a safe, private tunnel for your employees to connect through. They work best together.
How often should my firewall be updated?
At minimum, check quarterly. But firmware/software updates should be applied as soon as they’re available.
Can my in-house team set this up, or should I outsource?
If your team has IT training, maybe. But most small businesses find it’s easier (and safer) to have experts handle it so nothing gets overlooked.
Why Partner with IT Systems, LLC?
At IT Systems, LLC, we get that most small business owners, school leaders, or nonprofit directors don’t want to spend their day worrying about firewalls. You want peace of mind that your network is locked down so you can focus on what you do best.
Here’s what we bring to the table for West Michigan businesses:
- Right-sized solutions: We don’t sell you “enterprise” gear you’ll never use. We match firewalls to your actual business needs.
- Ongoing monitoring: We keep an eye on your network so threats are caught before they become disasters.
- Compliance support: Whether it’s HIPAA, FERPA, or another requirement, we help you stay audit-ready.
- Local expertise: We’re based here in Grand Rapids, serving small businesses, private schools, nonprofits, and healthcare practices across West Michigan.
👉 Ready to stop worrying about cyber threats? Contact IT Systems, LLC today to schedule a consultation and make sure your firewall - and your whole network - is working for you, not against you.