If you’re still running Windows 10 in 2026, we need to talk.
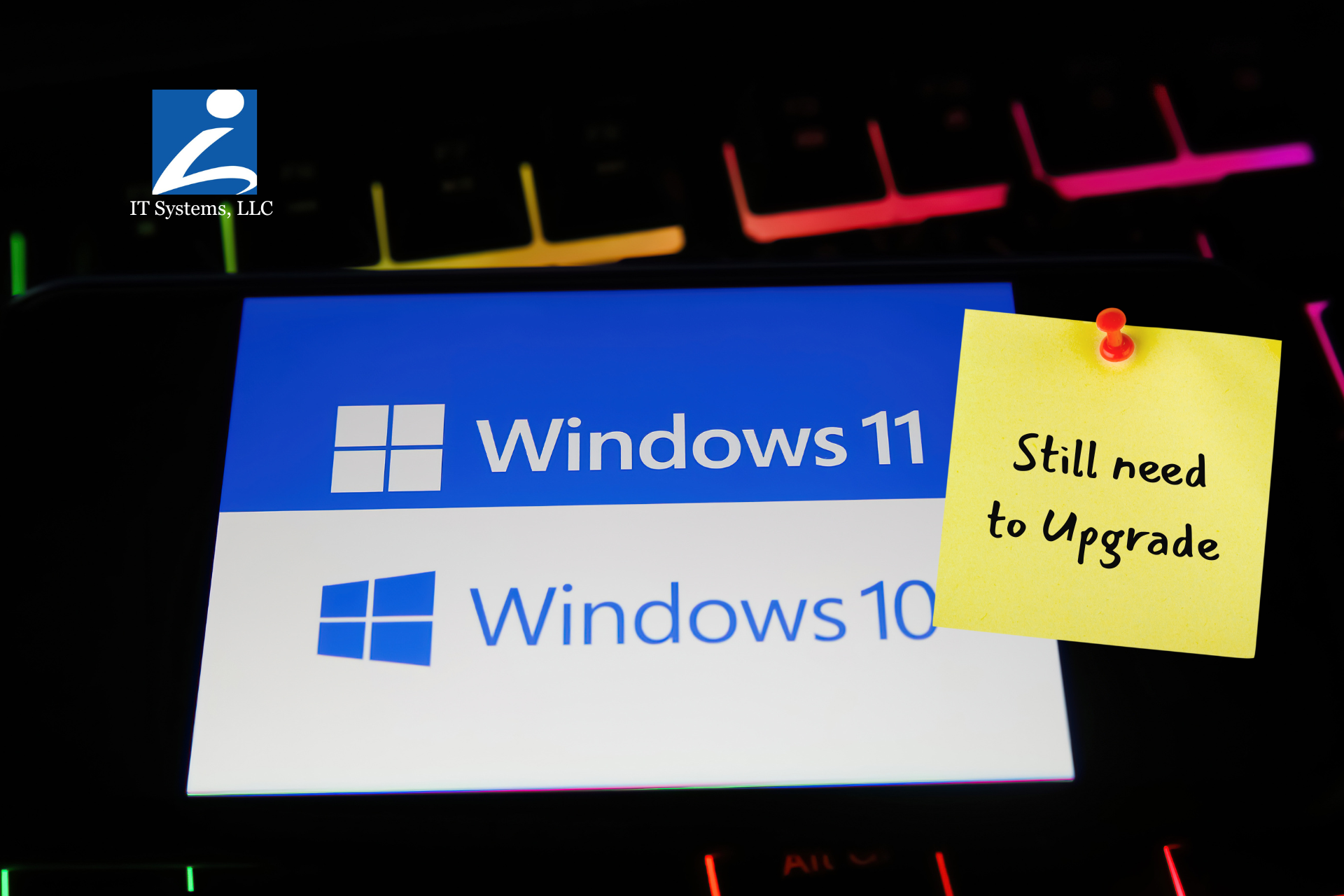
Fact: Windows 10 Has Reached End-of-Life. You’re Now On Your Own.
Microsoft officially ended support for Windows 10 on October 14, 2025. That means no more security patches, bug fixes, or support of any kind. If your business is still running Windows 10 in 2026, your systems are vulnerable, which means, so is your data.
Despite the warnings, millions of users continue to use Windows 10, thinking that 'it still works fine' is a good enough reason to keep it. According to a recent TechRadar report, a staggering number of businesses and individual users have yet to migrate.
'It Still Works' Isn’t a Security Strategy
Let’s call it what it is: wishful thinking. Just because Windows 10 boots up doesn’t mean it’s safe. The lack of updates means any future vulnerabilities discovered by hackers will go unpatched. Permanently.
At IT Systems LLC, we’ve talked with business owners who aren’t sure if the upgrade is necessary or who worry it will cost too much. But here’s the truth: sticking with outdated systems is usually more expensive in the long run.
What the Risks Really Look Like
In a post-support environment, Windows 10 becomes what cybersecurity experts call a 'sitting duck.'
Here’s what can go wrong:
- No patching means known exploits are open season for attackers
- Third-party software begins to drop compatibility
- Antivirus tools can’t rely on Windows APIs
- Compliance failures (especially for places like dental offices, small attorney practices, or anyone dealing with client records and compliance.)
The TechRadar article warns that unpatched systems are already a top target for botnets and ransomware, and that will only increase as support fades further in the rearview mirror.
What You Can Do Now
1. Know What You’re Working With
Start with a full IT audit. How many machines are still running Windows 10? What’s their age, performance, and compatibility with Windows 11?
2. Upgrade or Replace
Many systems can be upgraded to Windows 11. But if your devices are more than 4–5 years old, it might be time for a refresh. Newer hardware supports better security, faster performance, and often costs less to maintain.
💡 Need help evaluating devices? Check out our hardware and procurement services.
3. Plan the Migration Strategically
You don’t have to upgrade everything overnight. Start with the people who rely on their computers the most, like your front desk team, managers, or anyone handling billing, and roll out upgrades in waves to avoid disruption.
4. Don’t Forget Backups and Security
Upgrading an OS is the perfect time to check that backups are functioning, MFA is enabled, and endpoint protection is current. See our cybersecurity checklist.
Why Some Businesses Still Haven’t Upgraded
From what we’ve seen, here are the top reasons businesses stay on Windows 10:
- 'It still works fine'
- 'We don’t have the budget right now'
- 'We’re waiting to replace everything at once'
- 'We didn’t realize support already ended'
The common thread? Uncertainty. But uncertainty shouldn’t be your IT strategy. We can help you build a phased plan that fits your timing, your team, and your budget.
What Not to Do When Upgrading from Windows 10
We’ve seen the good, the bad, and the messy when it comes to Windows upgrades. If you want a smooth transition, here are a few common mistakes to avoid:
- Skipping a hardware check – Not all machines can run Windows 11. Trying to upgrade incompatible devices can lead to serious headaches.
- Forgetting to back up your data – This one’s big. Always back up before you start. If something goes sideways, you’ll thank yourself.
- Only upgrading part of your team – Leaving some staff behind on Windows 10 just creates confusion and compatibility issues.
- Assuming it’s plug-and-play – Drivers, legacy apps, and user settings often need attention. It's not always a one-click fix.
- Waiting until something breaks – Upgrading reactively costs more and takes longer. Be proactive.
FAQ: What Businesses Are Asking About Windows 11
Can I still use my Windows 10 machine after support ends?
Technically, yes…but you’re flying without a parachute. Without security patches, your system is exposed to known threats that hackers love to target.
Do I have to replace all our computers?
Not necessarily. Some older machines can handle Windows 11, but if they’re more than 4–5 years old, it may be smarter to replace rather than wrestle with upgrades.
What if we use custom software?
That’s something we plan for. We’ll assess compatibility and work with your vendors to ensure nothing breaks in the process.
How long does the upgrade take?
It depends on how many machines you have, but we typically phase upgrades to reduce downtime - often during off-hours to keep things running smoothly.
Can IT Systems, LLC handle everything?
Yes. From audits and hardware procurement to software migration and post-upgrade support, we’ve got you covered. This isn’t our first rodeo.
Why IT Systems, LLC Handles This Differently
We’re not here to upsell. We’re here to make sure your tech actually supports the way you do business. And we’re local, right here in West Michigan, so you don’t have to wait on hold with a national provider who doesn’t know your setup.
We’ve helped dozens of small businesses upgrade their systems, improve performance, and gain peace of mind. Often saving money in the process.
Let’s Talk About What’s Next (Not What You’re Stuck With)
You don’t have to figure this out alone. Whether you’re running five Windows 10 devices or fifty, we’ll help you make a smart, sustainable plan for what’s next.
👉 Schedule a Windows 11 readiness check
You Might Also Like:
🧠 Time’s Up for Windows 10: What Grand Rapids Businesses Need to Know
🔁 Cloud vs. On-Prem IT in 2026: What Works Now?
💾 Firewall Setup for Small Businesses